(Part I of VI – Technology)
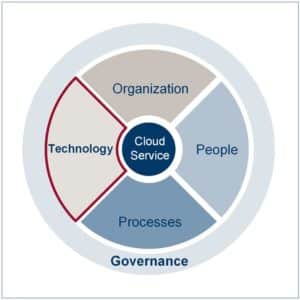 Having discussed the concept of a “Target Operating Model” recently, I want to outline the integration of Cloud Services into a TOM as a practical example of this concept in real life. As you may recall, the Target Operating Model consists of 6 Dimensions ( Governance, Services, Processes, Organization, People and Technology.)
Having discussed the concept of a “Target Operating Model” recently, I want to outline the integration of Cloud Services into a TOM as a practical example of this concept in real life. As you may recall, the Target Operating Model consists of 6 Dimensions ( Governance, Services, Processes, Organization, People and Technology.)
In the first part of the Cloud Service and TOM discussion, I want to focus on the Technology-Dimension.
The meaning of the TOM technology dimension, on a strategic, tactical and operational level is unequally distributed between a Cloud Service Provider and a Cloud Customer. Whereas for a cloud provider technology is one of the main components for the success of its business model, the Cloud Customer couldn’t care less, could he?
Surely, the fundamental drivers for the success of the cloud as a business model are the technology enabled resource pooling opportunities, powered by virtualization and broad network access. At the same time, exactly the same technology drivers are not coming for free as service added value for the consumers by taking away the management of specific risks from him. Specific risks related to technology will continue to play an important role in Cloud Computing especially in the current era of “Inflated expectations” (see picture below). Hundreds of new and rather immature cloud provider start-ups are going to hop on the rolling train of cloud computing trying to get a easy ride. Market consolidation during the upcoming era of “Disillusionment” is very likely to strengthen maturity. Until then, the following technology related constraints will continue to stay relevant for cloud consumers:
Shared technology vulnerabilities:
- The management of multipurpose and multi-tenancy architecture implementations is complex and hardly standardized in terms of operational procedures and automated tools. Instead of being confident, that this risk is being managed by the provider, the customer will have to have a look at the architectural governance elements of the cloud provider.
Insecure application interfaces:
- Very likely, existing proven technology elements will be migrated (or upgraded) from traditional models (i.e. client-server) to fancy cloud computing technology elements very hastily resulting in “not designed” for cloud computing security. This is especially becoming an issue if customers are looking for cross-cloud application data exchange.
Account, service and traffic hijacking:
- Despite all the good existing security standards, the increased exposure of enterprise data due to the success of cloud services is going to attract the usual suspects significantly. This issue cannot be left to be handled by the service provider alone.
As a conclusion, technology and architectural competencies will continue to be an area of concern for cloud customers and its retained IT organizations. The difference is that those competencies will have to be transferred form a purely operational level to a more strategic governance level overseeing Cloud Service portfolio integration and the definition of Cloud service design requirements.
Related Blog-Posts:
- Part I Target Operation Model – Technology
- Part II Target Operation Model – Governance
- Part III Target Operation Model – Services
- Part IV Target Operation Model – Processes
- Part V Target Operation Model – Organization
- Part VI Target Operation Model – People

Pingback: How To Ease Executives’ Concerns About Moving To The Cloud - Information Security Buzz